Cybersecurity Hands-on Education, Certification, and Knowledge. Our platform for hands-on training, advanced exercises, and cybersecurity skills certification.
CHECK was born from university research and field experience to address a concrete challenge: training cybersecurity professionals through hands-on practice. The platform offers virtual environments that replicate real infrastructures, allowing users to safely practice attack and defense scenarios.
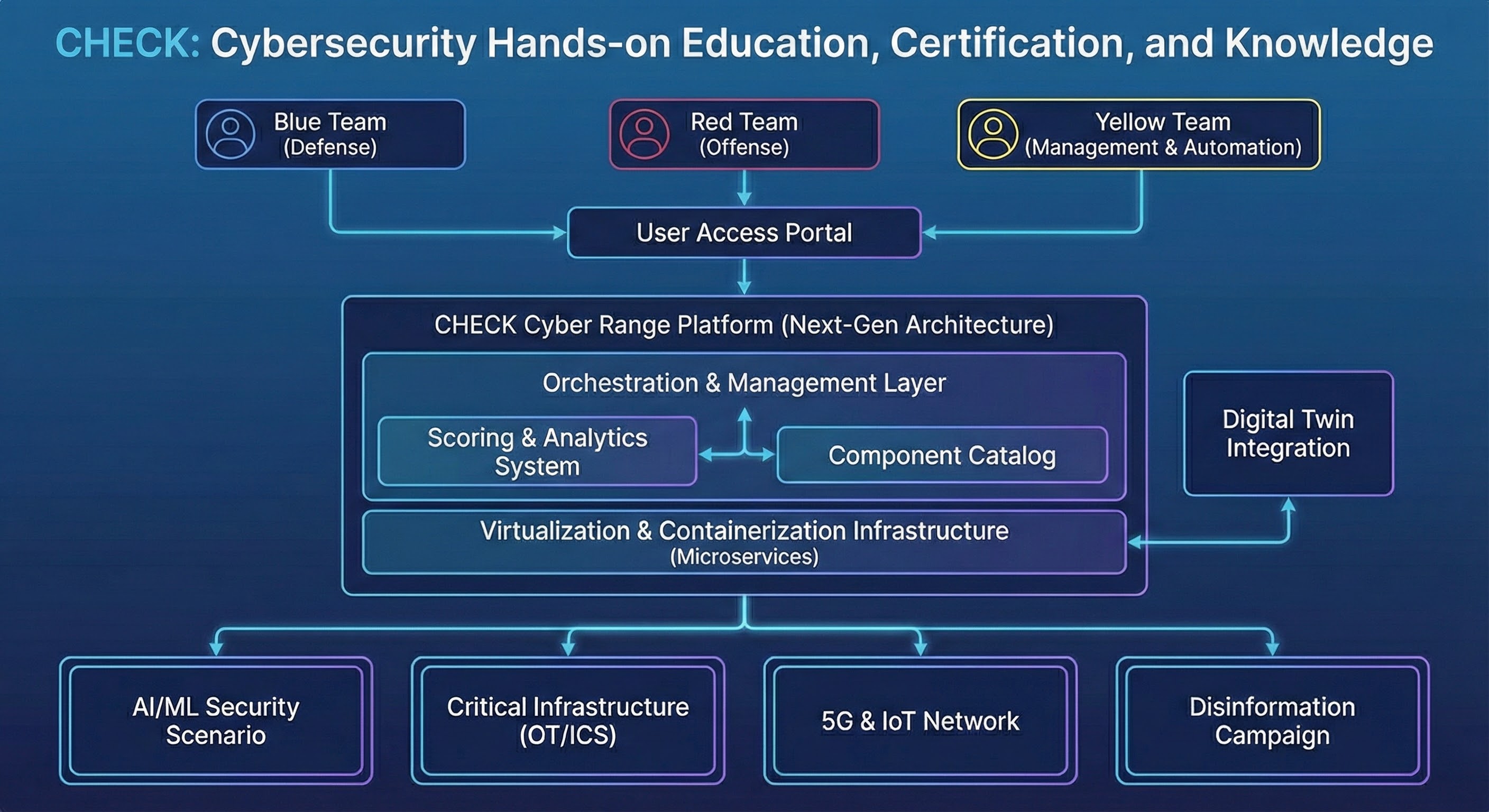
We replicate complete IT and OT infrastructures: enterprise networks, SCADA systems, industrial plants. Each scenario is designed to be indistinguishable from a real production environment.
We create faithful digital replicas of your real infrastructures. The Digital Twin allows you to test attack scenarios on the virtual copy without risks to production systems.
The Digital Twin approach comes from research in the ARTIC project within SERICS, funded by the Italian NRRP, and represents the state of the art in infrastructure simulation for cybersecurity.
The orchestration system automatically manages the scenario lifecycle: provisioning, configuration, execution and teardown. Scalability and reproducibility guaranteed.
Scoring system that evaluates participant actions in real-time. Objective metrics to measure acquired skills and progress in the training path.
Exercises on traditional enterprise networks: penetration testing, incident response, threat hunting. From initial compromise to persistence, through detection and response.
Specific simulations for industrial environments: SCADA system attacks, PLC manipulation, control network compromise. Training for those protecting critical infrastructures.
Our research on HoneyICS and physics-aware attacks has allowed us to develop extremely realistic OT scenarios, based on real threats observed in the industrial sector.
CHECK adapts to different training and operational needs
Hands-on training for IT and security teams. Customized scenarios based on your infrastructure and the specific threats in your industry.
Objective assessment of security skills through practical exercises. Detailed reports to document acquired competencies.
Competitions between attack and defense teams to test detection and response capabilities in realistic and controlled scenarios.
Contact us for a demo or to discuss your organization's training needs. We can create customized scenarios for your industry.
Request a demo